 An 18-year-old hacker gained admin access to Uber on September 15, 2022. These are the steps that the hacker took:
An 18-year-old hacker gained admin access to Uber on September 15, 2022. These are the steps that the hacker took:
- The hacker obtained an Uber employee’s phone number.
- He directed the employee to a phishing site that looked like an Uber login page. The employee logged in and the hacker gained his credentials.
- The hacker tried to get around the MFA by doing a Multi-Factor Authentication Fatigue attack. This attack consists of spamming MFA requests to the employee until he gets annoyed enough to allow the login attempt to go through.
- He continued the attack for over an hour before changing tactics. He contacted the employee on WhatsApp claiming to be on the IT team. He said that in order for the spamming to stop, he must accept the request.
- The employee accepted the request and the hacker gained access to the network.
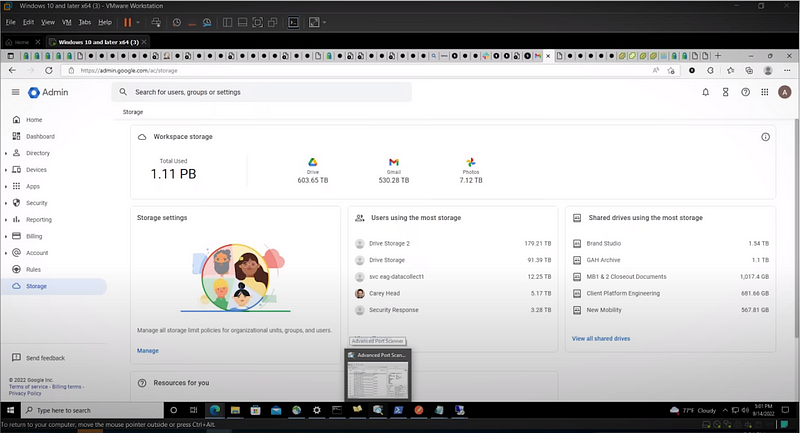
- The hacker found network shares with PowerShell scripts that contained hard-coded admin credentials.
- The hacker used the username and password of the admin to gain access to Amazon Web Services (AWS), GSuite, DA, DUO, OneLogin, Uber security dashboards, and their financial data.
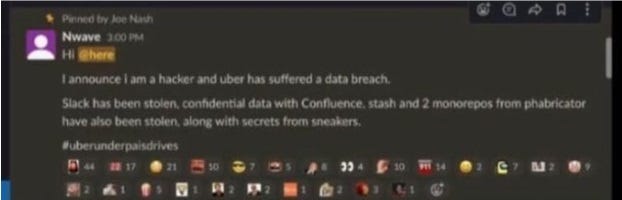
- He continued to vandalize reports on Uber’s HackerOne bug bounty program before declaring his presence in Uber’s Slack workspace.
 Aftermath
Aftermath
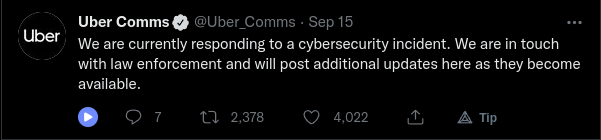
Uber’s stock prices dropped by 6% following the day of the breach, lowering its valuation by over $2 billion. The stock prices did eventually recover. Uber responded with a tweet on their PR Twitter account.
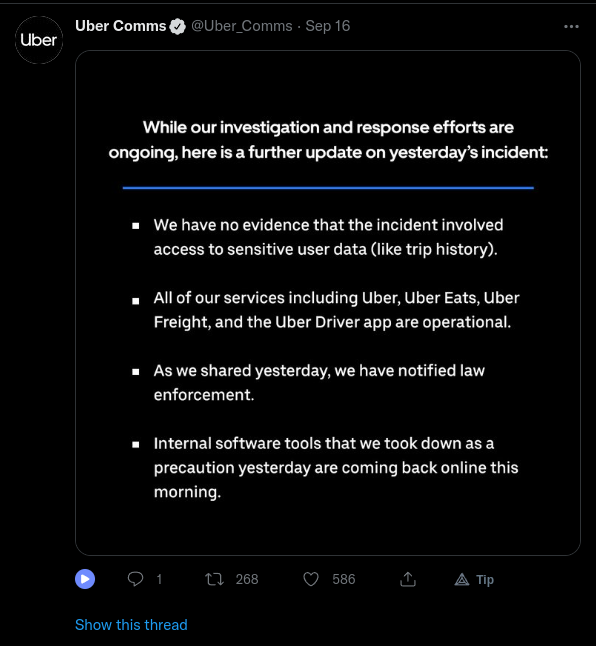
 Uber followed up by stating that there was no evidence of sensitive user data being stolen, they have notified authorities, and their internal and external applications are operational.
Uber followed up by stating that there was no evidence of sensitive user data being stolen, they have notified authorities, and their internal and external applications are operational.
 They also created a “Security Updates” page on their Uber Newsroom where they make posts about the developments in their investigation.
They also created a “Security Updates” page on their Uber Newsroom where they make posts about the developments in their investigation.
Shifting blame
Uber tried to shift the blame towards Lapsus$, an international hacker group that has conducted cyberattacks against large companies and government organizations such as Ubisoft, Nivida, Samsung, and Brazil’s Ministry of Health. It is speculated that Uber is attempting to make their hack less embarrassing by claiming it was done by a more elite organization.
Most Embarrassing Hack Ever?
This hack could have been completely avoided had better cybersecurity practices been instilled in Uber. Hard-coded credentials are among the 2022 CWE top 25 most dangerous software weaknesses. Any cybersecurity professional should be aware of the risk that is involved in having hard-coded credentials in an accessible share. In addition, the employee should not have had access to these sensitive network shares. This goes against the fundamental cybersecurity principle of least privilege. This hack is a learning opportunity of how important the fundamentals are when establishing cybersecurity in an organization.